IT Governance is everyone’s responsibility
With data breaches, ransomware attacks and other security risks dominating the headlines lately, it was perfect timing for IT governance to be the topic of this month’s AITP Atlanta meeting. Our speaker and subject matter expert, George Govantes, is an IT professional with more than 20 years of experience in information security, identity management, IT and data governance and risk.
I learned a ton from listening to George, some were just plain fascinating and some of it was incredibly terrifying. He not only spoke about IT governance as a whole but about how to change your company culture to avoid the risks of today’s volatile environment.
Here’s a brief recap, sans (most of) the tech speak.
What is IT governance?
According to Wikipedia, IT governance is a subset discipline of corporate governance, focused on information technology and its performance and risk management. Basically, it’s the processes that ensure the effective and efficient use of IT in enabling an organization to achieve its goals.
So, once you know what IT governance is, George says you should operationalize it. Governance should never be done in a silo. To truly impact change in your organization, everyone needs to understand it and then change the way things are done as a result.
Why should your entire company care?
Simply put, people are usually at the heart of the issues with IT governance. And according to the Ponemon Institute’s Cost of a Data Breach Report, in 2020, data breaches on average cost $3.86 million. As an IT leader that might scare you – and it should.
One of the most recent security breaches with Colonial Pipeline was due to hackers using a compromised password (aka human error). The company suffered a ransomware cyberattack that impacted computerized equipment managing the pipeline. Shortly after, McDonald’s was hit by a data breach, exposing customers’ personal data. It was quickly contained, but still a nightmare for any business.
I could go on and on with stories of security issues, but you know as I do, there are too many to talk about. It all boils down to this: in a perfect world, everyone becomes part of the security team and the solution.
Symptoms of the problem
As we all need to be part of the solution, we all should know where the biggest vulnerabilities lie. The Open Web Application Security Project (or OWASP) monitors and reports the most common application vulnerabilities. The latest list was released in 2017. Here are the top 10:
- Code injection – when an attacker sends invalid data to the web application with the intention to make it do something that the application was not designed/programmed to do.
- Broken authentication – can allow an attacker to use manual and/or automatic methods to try to gain control over any account they want in a system – or even worse – to gain complete control over the system.
- Sensitive data exposure – one of the most widespread vulnerabilities on the OWASP list and one of the most common attacks around the world. It consists of compromising sensitive data that should have been protected such as credit card numbers, social security numbers, medical information and more.
- XML external entities (XXE) – a type of attack against an application that parses XML input. This attack occurs when XML input containing a reference to an external entity is processed by a weakly configured XML parser.
- Broken access control – in website security, access control means putting a limit on what sections or pages visitors can reach. Broken access gives users visibility to parts of your website they shouldn’t be seeing.
- Security misconfigurations – Brute force (the act of trying many possible log-in combinations) can be more successful by exploiting these security misconfigurations: unpatched flaws, default configurations, unused pages, unprotected files and directories and unnecessary services.
- Cross-site scripting (XSS) – a widespread vulnerability that affects many web applications. XSS attacks consist of injecting malicious client-side scripts into a website and using the website as a propagation method.
- Insecure deserialization – the process of serialization is converting objects to byte strings. And deserialization is converting byte strings to objects. If an attacker can deserialize an object successfully, then modify the object to give himself an admin role and serialize it again. This set of actions could compromise the whole web application.
- Using components with known vulnerabilities – failing to update every piece of software on the backend and frontend of a website will introduce heavy security risks. Running out-of-date software can leave it unprotected.
- Insufficient logging and monitoring – not having an efficient logging and monitoring process in place can increase the damage of a website compromise.
Learning from other industries
According to George, IT governance doesn’t have a great track record of learning from other industries. As a result, the same issues keep happening over and over again – malware, ransomware, data breaches, etc. He gave examples of how the aviation and medical industries have learned from their past.
In 1953, Three Comets aircraft fell apart in the air, killing 43 people. The cause – square windows that couldn’t take the pressurization and depressurization while in flight. The solution – round windows that keep planes from disintegrating mid-flight. The discovery after a thorough investigation was a major milestone in aviation safety.
In the medical industry, Ignaz Philipp Semmelweis was a Hungarian physician and scientist, known as an early pioneer of antiseptic procedures. Described as the “savior of mothers,” Semmelweis discovered that the incidence of puerperal fever could be drastically cut by using hand disinfection in obstetrical clinics. And it worked.
But wait, there’s more
The other issue in IT governance is that the current governance models are outdated. And they don’t include the human factor, which is a significant oversight (see the earlier example with Colonial Pipeline).
Problems with current approaches to governance
Command and control model
- Manages, checks and controls
- Hires based on experience, track record and qualifications. Managers, Directors and VPs are expected to be the subject matter experts.
- Managers give directions often without prior consultation and may not be aware of the latest practices and features of a solution.
The key results of this model
- It does not scale, by not leveraging input and a team’s capabilities.
- It assumes Managers, Directors and VPs are the subject matter experts in the latest technology and not the team members working closest to it.
Advantages of moving away from the command-and-control leadership model
- Individual team members are part of the solution, encouraging ownership and adoption of the governance, risk management and compliance (GRC) program.
- It encourages feedback on problem areas.
- It increases accountability where it belongs.
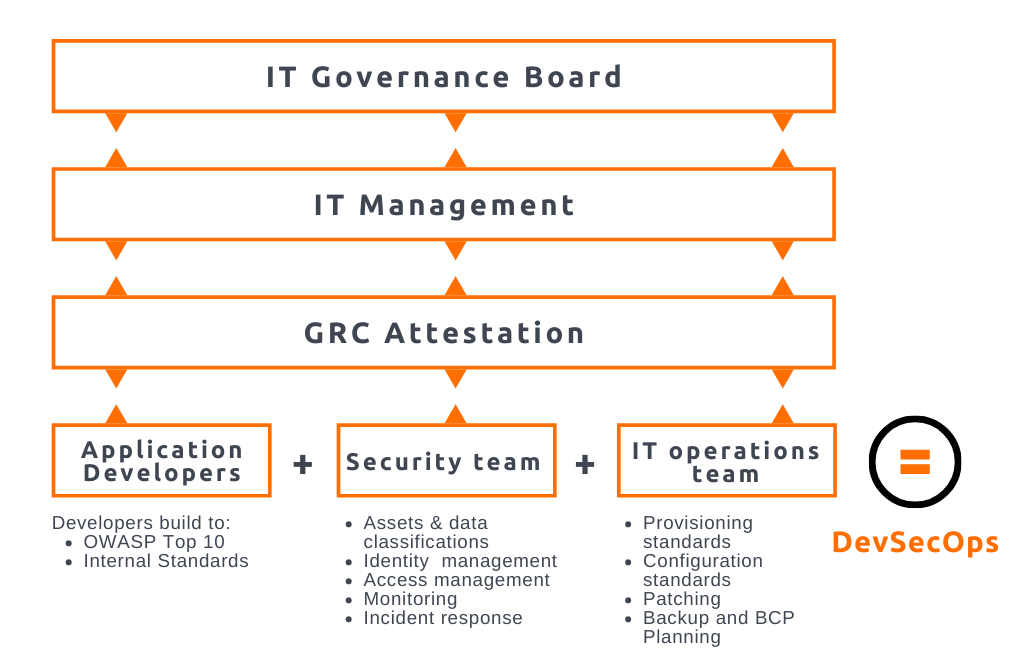
The ideal IT governance model, according to George, is as follows:
Still not convinced?
I’ll tell you one more scary story that George referenced to show just how devious these crimes can get. Criminals are pivoting their scams as companies tighten their security.
In 2019 in the UK, criminals used artificial intelligence-based software to impersonate a CEO’s voice and demand a fraudulent transfer of €220,000 ($243,000). The CEO thought he was speaking on the phone with his boss, the chief executive of the firm’s German parent company, who asked him to send the funds to a Hungarian supplier. Whoever was behind this incident appears to have used AI-based software to successfully mimic the German executive’s voice by phone. And according to George, cybercriminals only need three seconds of your voice to reproduce it. Terrifying but true.
In summary
Selling security to your organization is very difficult, but it can be done. Companies sometimes spend thousands of dollars on a solution that doesn’t actually do anything for their organization and then sits on a shelf (metaphorically). Understanding what you’re getting out of a tool can end up saving you money. And even spending your IT budget on something useful – like security measures – can have extremely valuable benefits in the long run.
About the author
Steven Wright serves as a Senior Account Executive for Synergis and volunteers his time as President of the Atlanta chapter of the Association of Information Technology Professionals. Steve has had a career in technology, spanning more than 25 years. He has always served in an advisory, and relationship development capacity, working within sales and business development groups for healthcare technology outsourcing, manufacturing, professional service, and, most recently, the staffing industry. In his free time, Steve enjoys learning about new and emerging technologies. This love of tech has helped him aid clients and candidates alike in their career and talent journeys.
Share this article
Let's get started.
"*" indicates required fields
